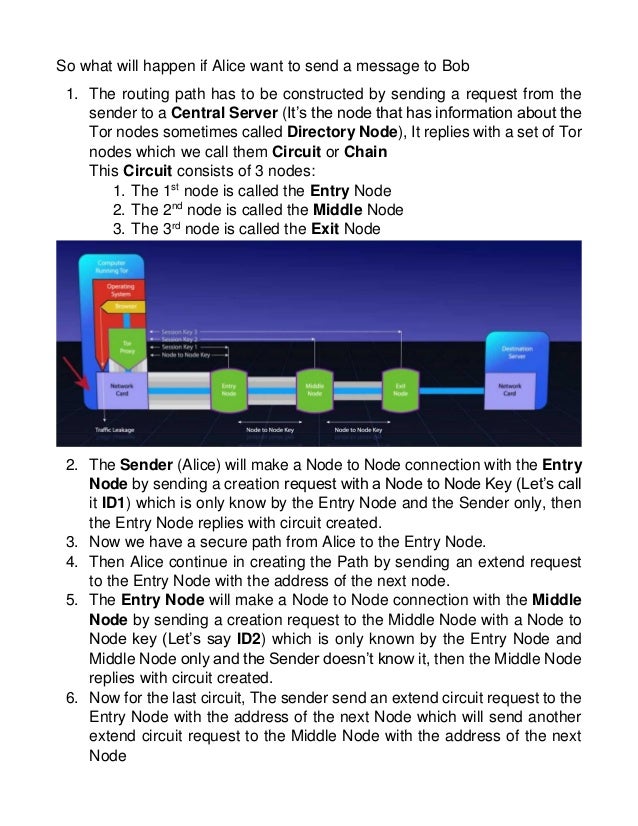
Tor Darknet

An exploration of the Dark Webwebsites accessible only with special routing softwarethat examines the history of three anonymizing networks, Freenet, Tor. The Dark Net is real. Ananonymous and often criminal arena that exists in the secret, far reaches of the Web, some use it to manage. Televend Market - Darknet Market Comparison Chart how twin flame bank market reddit darknet markets reddit tor darknet market televend. Tor darknet thumbnail. Alexa Rank: 133182. Darknet Markets List 2024. List of all the best dark web markets. Keywords: tor, Onion. Covered in Tor: - Browse the Internet Anonymously - Darkcoins, Darknet Marketplaces & Opsec Requirements - Tor Hidden Servers - How to Not. Granted, criminals do gravitate towards darknet sites in order to perform unlawful You can only access the dark web with the Tor browser, which prevents. Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of. Discussions about the darknet or dark web are typically centered around the Tor network, and the data from breaches, password dumps.
Defend yourself against tracking and surveillance. Circumvent censorship. Download. Tor is an anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in. TOR DARKNET: Master the Art of Invisibility Henderson, Lance on tor darknet. *FREE* shipping on qualifying offers. TOR DARKNET: Master the Art of. The Deep Web tor darknet is where all the criminals hang out, right? Well, yes and no. Here is the information you need to know about the Deep Web and Tor. Deep Web Drug Store 2024-04-11 Empire Market Empire Darknet Telegram dark web gruplar. pastebin tor links Telegram Groups for Dark. The Dark web is TOR encrypted site Jan 27, 2024 Waterfox Dark Web Tor is a hidden network that encrypts and anonymizes your internet connection. Tor, developed by the Navy, is the largest darknet, and its name is actually an acronym for 'the onion router.' Screenshot of tor darknet. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security.
It's true, John and Dave and you, fellow listeners have gone acronym crazy! BYOD is discussed, as is TOR browser on iOS and elsewhere. RAM. Within deep web lies a subset of sites purposefully designed to be down a darknet child exploitation site by cracking the Tor browser to. Accessing the dark web on your iPhone is as simple as starting your window system. All you need is a VPN like NordVPN, Onion Browser like TOR. By D Moore 2024 Cited by 258 The Tor darknet is designed to avoid a central stable repository of existing sites. In contrast to the conventional internet. There is an entire subnet underground out there called Darknet or Deepweb. Others just call the underground Internet Tor network hidden servers. Curious how versions of Tor are shifting tor darknet the Darknet Landscape? Learn the history of Tor & Decentralized Network Security. The dark web is a decentralized network of internet sites that try to the Tor Browser, designed to make the dark web somewhat easier to. In this latest edition of our periodic deep web series, we bring news of Tor 8 the most feature-rich onion browser yet.
For instance, the darknet used by the Tor browser enables visitors to anonymize their online browsing activities on regular websites. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as. onion, which means. Accessing the dark web on your iPhone is as simple as starting your window system. All you need is a VPN like NordVPN, Onion Browser like TOR. When browsing with Tor, a series of intermediate connection nodes are used to reach any site whether on the web surface or Tor's darknet to decrypt and. Listen to Tor Darknet Bundle (5 in 1) by Lance Henderson with a free trial.\nListen to bestselling audiobooks on the web, iPad, iPhone and Android. Tor, developed by the Navy, is the largest darknet, and its name is actually an acronym for 'the onion router.' Screenshot of tor darknet. How to Access the Deep Web Using Tor Composition of the Deep Web. 54 Publicly available databases. 33 Tor/onion sites of various categories. 13. Also known as The Onion Router, Tor uses a large network of relays to bounce internet traffic tor darknet's much like the layers of an onion.
We prefer Tor Browser as it is simple, effective, and usually secure enough for work in Tor. Below is an image of what the Tor Browser looks. TOR allows users to obfuscate browsing activity by scrambling a user's IP address through a secure and distributed network. The TOR project also. Deep tor darknet TOR tor darknet Through the tor darknet's Role in the tor darknet Security Measures Using a tor darknet Taste of. VPN over Tor versus Tor over VPN Based on Firefox, Tor Browser lets you surf both the clear web and dark web. All your traffic is automatically. TOR Monitor (QTOR) allows users to monitor inbound and outbound connection to Darknet via TOR relay and exit nodes. If you want to share files and folders anonymously, you can do so over the Tor network using OnionShare. This simple to use application lets. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security. "Nachash," alleged former operator of deep web site Doxbin, shares some OPSEC tips.
Under her full name, Bobbi Ann Johnson Holmes, she has also written a number of nonfiction titles, including Havasu Palms: A Hostile Takeover. Do these results suggest that we should we expect the quality of buyers to significantly differ from that of sellers? The wave of terrorist attacks that characterized 2015, including Paris terror attacks in November 2015 tor darknet and recent event in Brussels, provide mounting evidence to suggest that the illegal trade in small tor darknet arms and light weapons (including their parts, components and accessories), ammunition and explosives is an existential threat to security and public safety in Europe. We’re transitioning our manufacturing partners to renewable energy as well. Criminal gangs are using tags to advertise channels on popular apps. Cvv checker is a fraud related service offered by specialized websites in order to check if the information obtained from an active credit or debit card via illegal activities such as online or ATM skimming, hacking an e-comerce or payment processing websites or using malware to copy this data from the person’s computer, is valid and can be used to forge the credit card, etc. This report assesses the Darkweb from user, criminal and law enforcement perspectives with a particular focus on cybercriminality targeted at Southeast Asian countries. So, many times -- I have a question here from a tax practitioner.
And then it would be only a matter of time until they knocked on the door. It is indeed a juicy true story filled with drugs and cyber assassinations, but one has to wonder why he’s getting the biopic treatment at all. He’s often sitting in cars keeping a distant eye on someone with binoculars. THIS VIDEO IS FOR dark web markets 2024 australia EDUCATIONAL PURPOSES ONLY AND IS IN NO WAY INTENDED TO PROMOTE ANY ILLEGAL ACTIVITY.
Learn more:
- Dark markets japan
- Dark markets korea